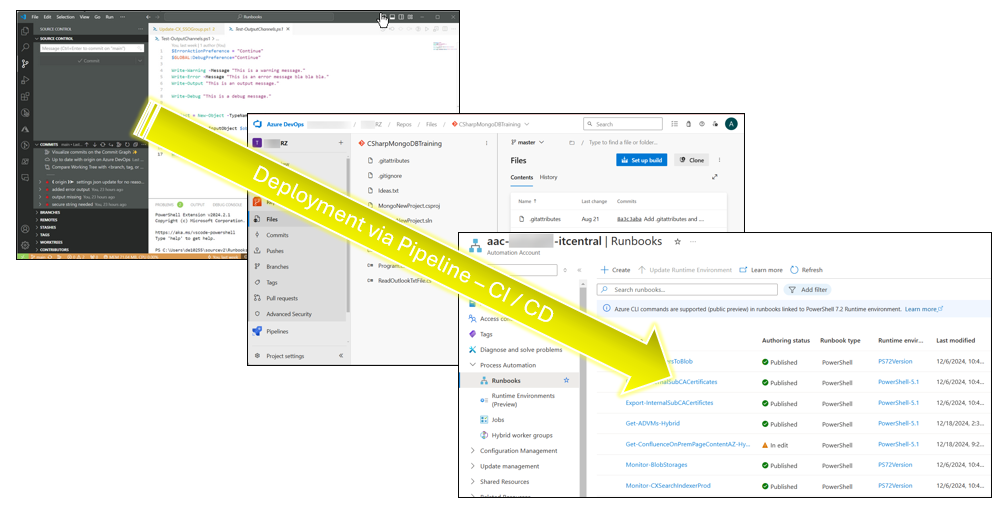
Azure Automation provides seamless integration with Azure DevOps and other Version Control Systems. Having change-tracking and … Connect Azure Automation to Azure DevOps as script repositoryRead more
PowerShell
Choosing between Azure Automation and Function Apps
Azure Automation and Function Apps offer server-less script execution. This post explains key differences between Azure … Choosing between Azure Automation and Function AppsRead more
Evolve from Scheduled Tasks to Azure Automation or Function Apps
Scheduled Tasks have been around since the early days of Windows Server. The task scheduler is … Evolve from Scheduled Tasks to Azure Automation or Function AppsRead more
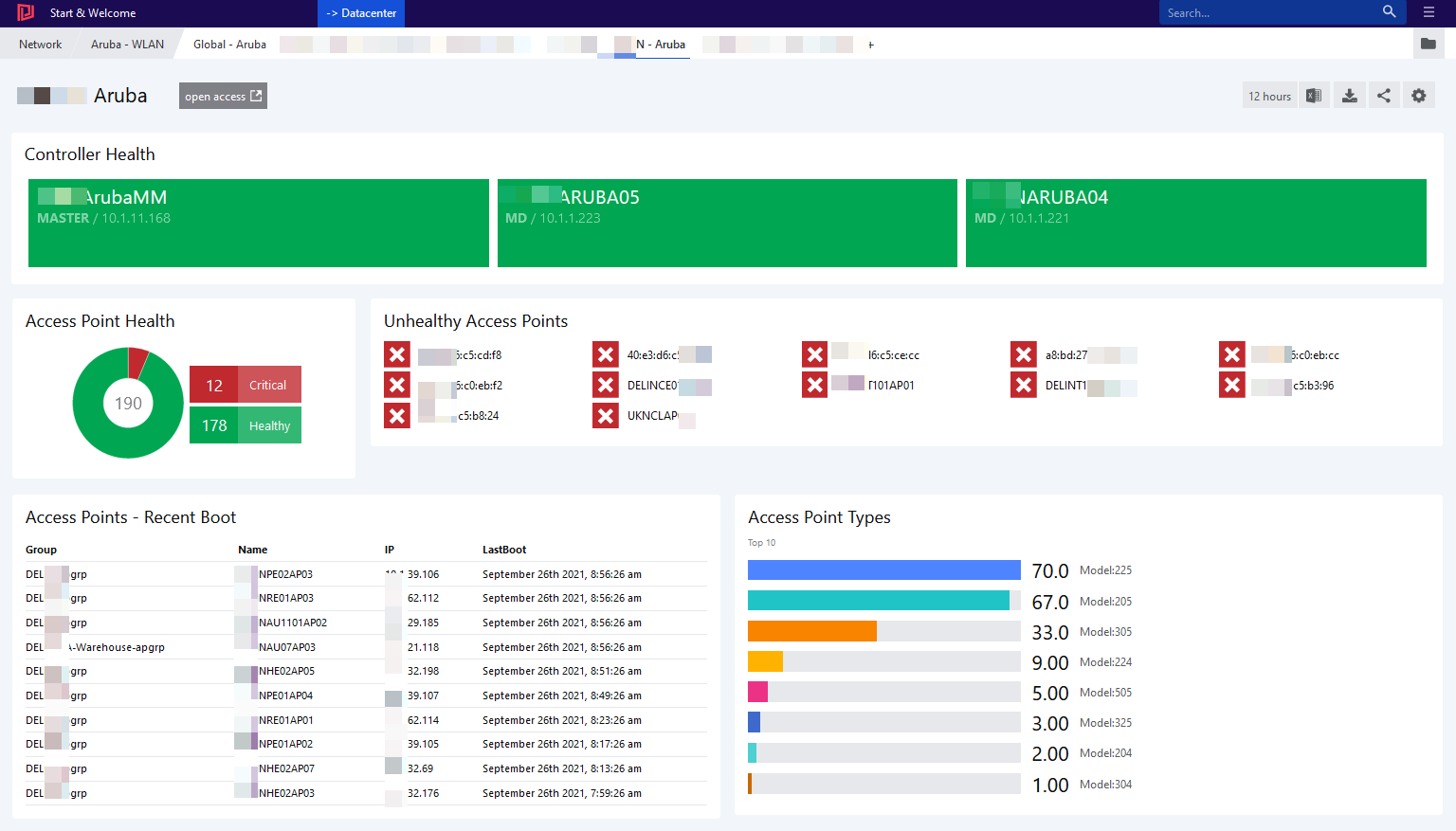
Visualize Aruba Wireless Infrastructure with Squared Up
Aruba Wireless technology is one of the market leaders. Squared Up can bring in visibility and … Visualize Aruba Wireless Infrastructure with Squared UpRead more
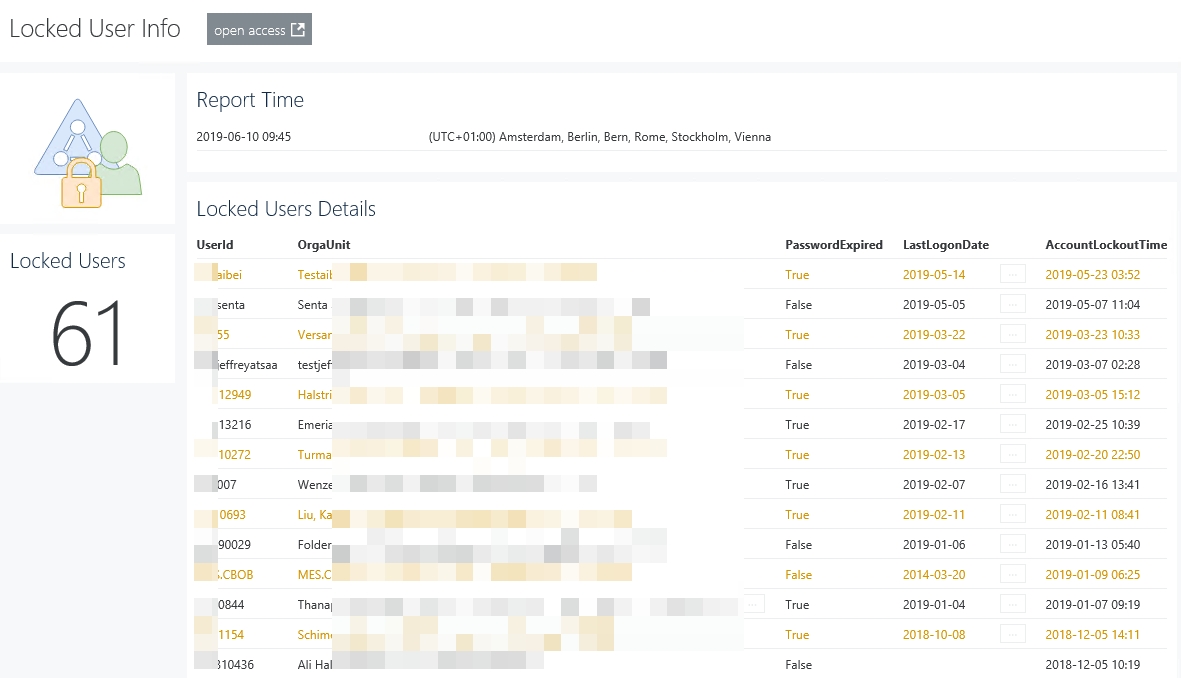
Squared Up dashboard for locked Active Directory Users – Only in PowerShell
Introduction Squared Up’s Web-API tile allows it to integrate information from any web-service that returns JSON … Squared Up dashboard for locked Active Directory Users – Only in PowerShellRead more