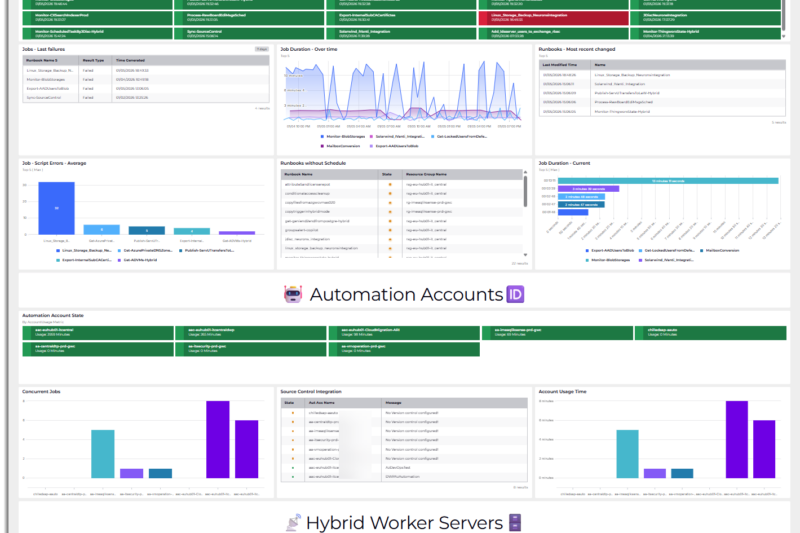
Observability turns scattered telemetry into actionable signals. This post doesn’t walk through building the dashboard UI … Azure Automation Dashboard – Code‑FirstRead more
Azure
Observability for Azure Virtual Desktop
Learn how I built a clean, insight‑packed Azure Virtual Desktop dashboard using SquaredUp Cloud —powered by … Observability for Azure Virtual DesktopRead more
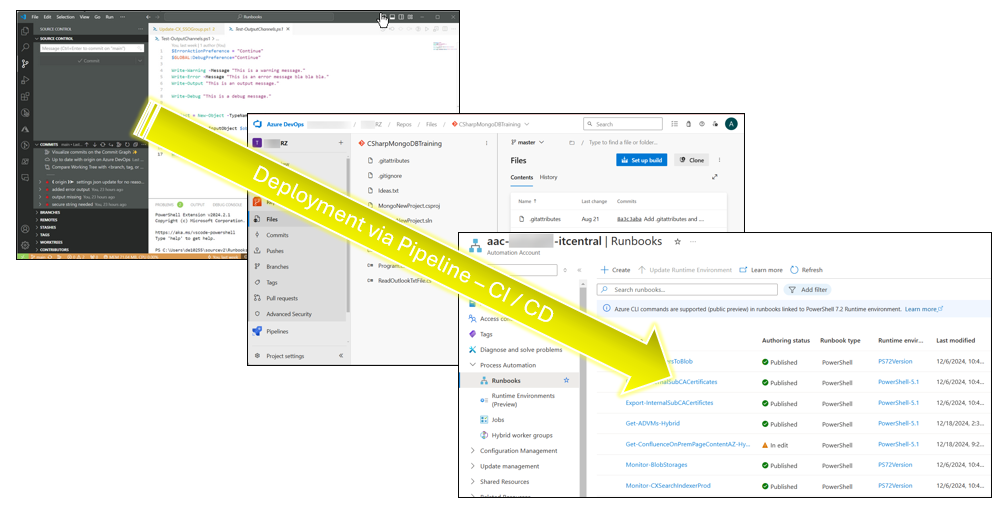
Connect Azure Automation to Azure DevOps as script repository
Azure Automation provides seamless integration with Azure DevOps and other Version Control Systems. Having change-tracking and … Connect Azure Automation to Azure DevOps as script repositoryRead more
Choosing between Azure Automation and Function Apps
Azure Automation and Function Apps offer server-less script execution. This post explains key differences between Azure … Choosing between Azure Automation and Function AppsRead more
Evolve from Scheduled Tasks to Azure Automation or Function Apps
Scheduled Tasks have been around since the early days of Windows Server. The task scheduler is … Evolve from Scheduled Tasks to Azure Automation or Function AppsRead more
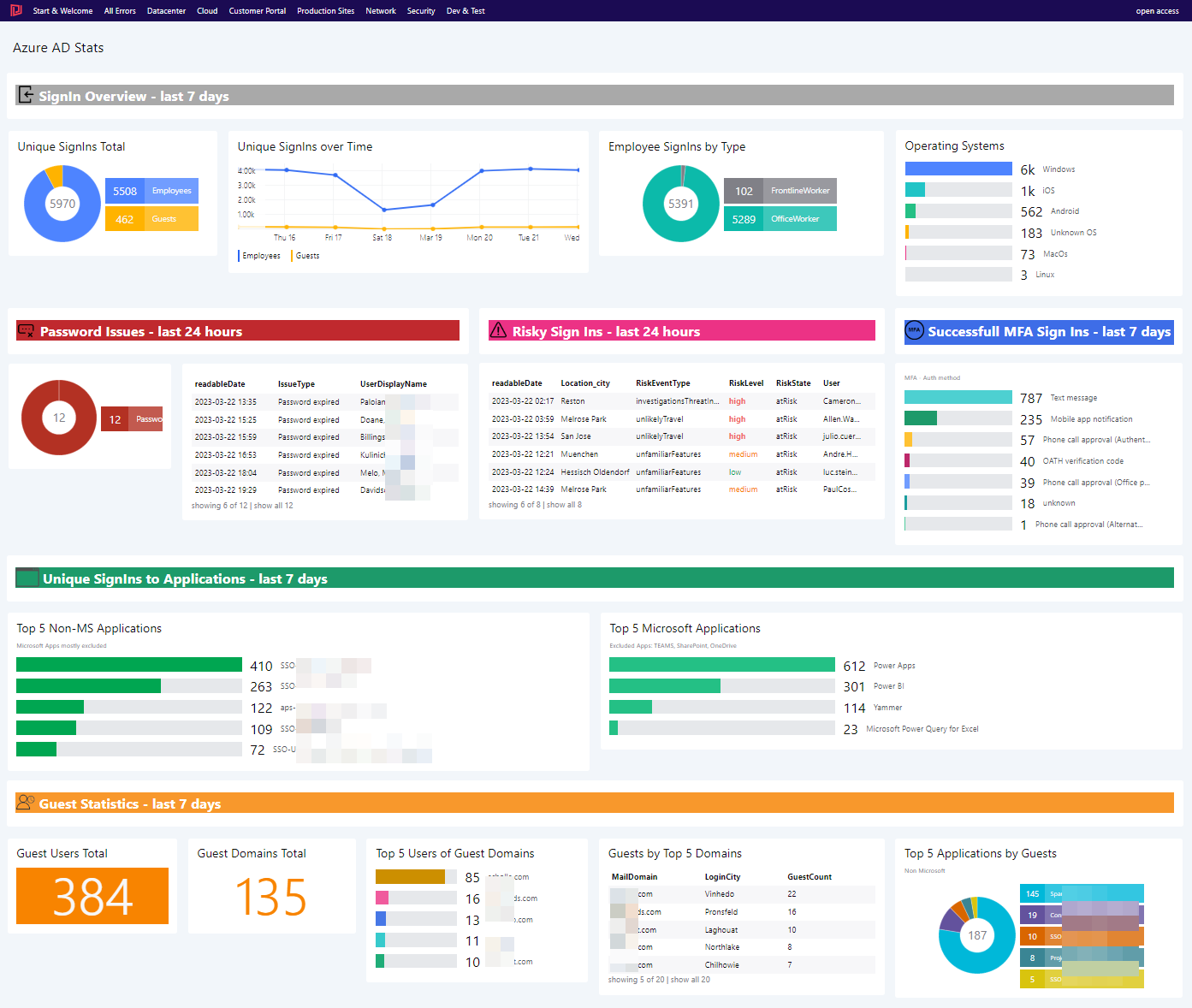
Understand your #AzureAD Sign-Ins with #KQL
Teaser When Azure AD is configured to record Sign-In activity, #Kusto can be used to gain … Understand your #AzureAD Sign-Ins with #KQLRead more